Updated on 20th October 2025
Updated on 20th October 2025
Trust Centre
BeatpulseLabs is committed to delivering secure AI inferencing and content categorization that meet the needs of customers, from individuals to large organizations.
While BeatpulseLabs has always taken the security of its products seriously, the importance of embedding security and privacy into the development life cycle has increased as BeatpulseLabs incorporates Artificial Intelligence capabilities in a responsible manner. This document summarizes key aspects of BeatpulseLabs's Secure Development Life Cycle (SDLC).
Company: Beatpulse Inc.
Website: www.beatpulselabs.com
Support email: support@beatpulselabs.com
Mailing address: Aldwych House, 71-91 Aldwych, London WC2B 4HN, United Kingdom
BeatpulseLabs is committed to delivering secure AI inferencing and content categorization that meet the needs of customers, from individuals to large organizations.
While BeatpulseLabs has always taken the security of its products seriously, the importance of embedding security and privacy into the development life cycle has increased as BeatpulseLabs incorporates Artificial Intelligence capabilities in a responsible manner.
This document summarizes key aspects of BeatpulseLabs's Secure Development Life Cycle (SDLC).
Company: BeatpulseLabs Inc.
Website: www.beatpulselabs.com
Support email: support@beatpulselabs.com
Mailing address: Aldwych House, 71-91 Aldwych, London WC2B 4HN, United Kingdom
BeatpulseLabs is committed to delivering secure AI inferencing and content categorization that meet the needs of customers, from individuals to large organizations.
While BeatpulseLabs has always taken the security of its products seriously, the importance of embedding security and privacy into the development life cycle has increased as BeatpulseLabs incorporates Artificial Intelligence capabilities in a responsible manner.
This document summarizes key aspects of BeatpulseLabs's Secure Development Life Cycle (SDLC).
Company: BeatpulseLabs Inc.
Website: www.beatpulselabs.com
Support email: support@beatpulselabs.com
Mailing address: Aldwych House, 71-91 Aldwych, London WC2B 4HN, United Kingdom
1. Software & Security Policy
Governance Security policies spanning the company are set at the corporate level by the corporate security team’s Chief Information Security Officer (CISO), while privacy policies are set by the Chief Privacy Officer (CPO) within the Legal team. BeatpulseLabs’s Human Resource team ensures that all employees are appropriately vetted before onboarding.
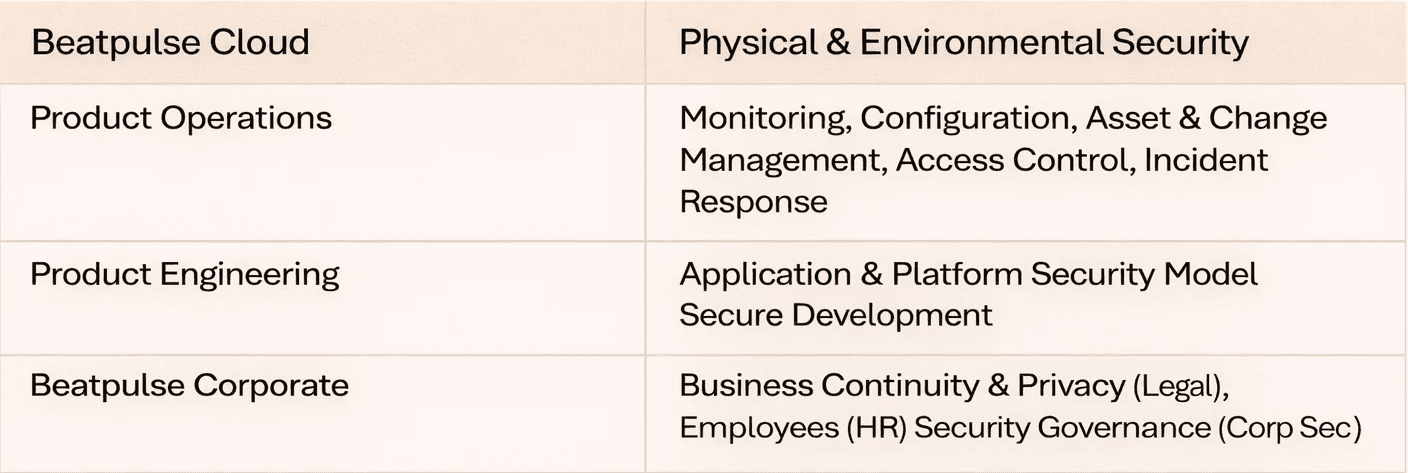
Corporate security controls are inherited across BeatpulseLabs, while functional areas (such as engineering and operations) are responsible for specific security control families, as seen in figure 1 below. The security of BeatpulseLabs products and services is overseen by the Chief Information Security Officer (CISO)- Products, who leads BeatpulseLabs's Software Security & Privacy team. This team is embedded within product operations and engineering, providing security guidance and validation while fostering a security & privacy champion program across the broad spectrum of product teams to help further embed security and privacy across BeatpulseLabs products.
Table 1: Product Security Responsibility by Functional Area
Governance Security policies spanning the company are set at the corporate level by the corporate security team’s Chief Information Security Officer (CISO), while privacy policies are set by the Chief Privacy Officer (CPO) within the Legal team. BeatpulseLabs’s Human Resource team ensures that all employees are appropriately vetted before onboarding.
Corporate security controls are inherited across BeatpulseLabs, while functional areas (such as engineering and operations) are responsible for specific security control families, as seen in figure 1 below. The security of BeatpulseLabs products and services is overseen by the Chief Information Security Officer (CISO)- Products, who leads BeatpulseLabs's Software Security & Privacy team. This team is embedded within product operations and engineering, providing security guidance and validation while fostering a security & privacy champion program across the broad spectrum of product teams to help further embed security and privacy across BeatpulseLabs products.
Table 1: Product Security Responsibility by Functional Area
Governance Security policies spanning the company are set at the corporate level by the corporate security team’s Chief Information Security Officer (CISO), while privacy policies are set by the Chief Privacy Officer (CPO) within the Legal team. BeatpulseLabs’s Human Resource team ensures that all employees are appropriately vetted before onboarding.
Corporate security controls are inherited across BeatpulseLabs, while functional areas (such as engineering and operations) are responsible for specific security control families, as seen in figure 1 below. The security of BeatpulseLabs products and services is overseen by the Chief Information Security Officer (CISO)- Products, who leads BeatpulseLabs's Software Security & Privacy team. This team is embedded within product operations and engineering, providing security guidance and validation while fostering a security & privacy champion program across the broad spectrum of product teams to help further embed security and privacy across BeatpulseLabs products.
Table 1: Product Security Responsibility by Functional Area


2. Secure Development Standards
2. Secure Development Standards
BeatpulseLabs utilizes the Building Security In Maturity Model (BSIMM) as the backbone to measure its efforts to immerse security throughout the development life cycle in the most effective manner for its products. BSIMM was utilized to create BeatpulseLabs’s Product Security Baseline to assure basic security and privacy requirements are addressed. The amount of security validation incorporated during the life cycle for a product varies depending on the product's relative risk.
BeatpulseLabs designs security into Beatpulse’s Software to ensure a consistent, secure experience across your enterprise, whether it's providing role-based access control (RBAC), logging, authentication, or authorization. BeatpulseLabs’s Software is also designed to integrate into your organization's security infrastructure through support of standards such as LDAP, SAML, OpenID, and even using your organization's identity store and security policies at the web level to facilitate single sign-on or public key infrastructure (PKI) support. Additional embedded product security capabilities are documented in the BeatpulseLabs’s Software Trust Center (beatpulselabs.com/trust) as well as our online help.
BeatpulseLabs provides secure coding training based on Open Web Application Security Project (OWASP) guidelines and promotes awareness of the Common Weakness Enumeration (CWE/SANS) Top 25 most dangerous software errors. BeatpulseLabs provides teams with secure coding checklists to further reinforce the importance of key security items that all product teams should address. Basic items, such as malicious code discovery, have been incorporated into the build process for many years, utilizing multiple antivirus programs to minimize risk and false positive alerts.
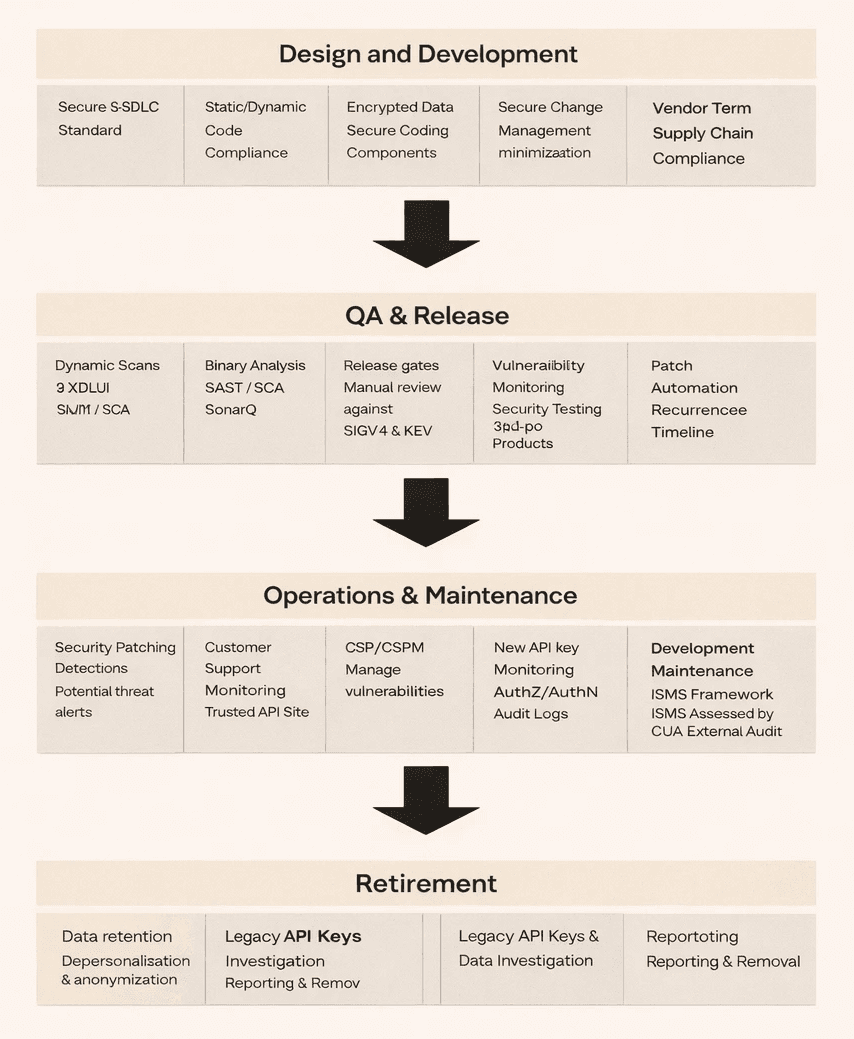
BeatpulseLabs applies its most rigorous security measures for its foundational products of BeatpulseLabs's Software Enterprise, Software Online, and Software Pro. These products regularly undergo static code analysis, dynamic scans, third-party component analysis, and periodic third-party pen testing.
BeatpulseLabs continues to expand the amount of security validation it performs against all BeatpulseLabs’s Software products and seen in table 2 below.
Table 2: Key Attributes of BeatpulseLabs’s Security & Privacy Development Lifecycle
BeatpulseLabs utilizes the Building Security In Maturity Model (BSIMM) as the backbone to measure its efforts to immerse security throughout the development life cycle in the most effective manner for its products.
BSIMM was utilized to create BeatpulseLabs’s Product Security Baseline to assure basic security and privacy requirements are addressed. The amount of security validation incorporated during the life cycle for a product varies depending on the product's relative risk.
BeatpulseLabs designs security into Beatpulse’s Software to ensure a consistent, secure experience across your enterprise, whether it's providing role-based access control (RBAC), logging, authentication, or authorization. BeatpulseLabs’s Software is also designed to integrate into your organization's security infrastructure through support of standards such as LDAP, SAML, OpenID, and even using your organization's identity store and security policies at the web level to facilitate single sign-on or public key infrastructure (PKI) support.
Additional embedded product security capabilities are documented in the BeatpulseLabs’s Software Trust Center (beatpulselabs.com/trust) as well as our online help.
BeatpulseLabs provides secure coding training based on Open Web Application Security Project (OWASP) guidelines and promotes awareness of the Common Weakness Enumeration (CWE/SANS) Top 25 most dangerous software errors.
BeatpulseLabs provides teams with secure coding checklists to further reinforce the importance of key security items that all product teams should address. Basic items, such as malicious code discovery, have been incorporated into the build process for many years, utilizing multiple antivirus programs to minimize risk and false positive alerts.
BeatpulseLabs applies its most rigorous security measures for its foundational products of BeatpulseLabs's Software Enterprise, Software Online, and Software Pro. These products regularly undergo static code analysis, dynamic scans, third-party component analysis, and periodic third-party pen testing.
BeatpulseLabs continues to expand the amount of security validation it performs against all BeatpulseLabs’s Software products and seen in table 2 below.
Table 2: Key Attributes of BeatpulseLabs’s Security & Privacy Development Lifecycle
BeatpulseLabs utilizes the Building Security In Maturity Model (BSIMM) as the backbone to measure its efforts to immerse security throughout the development life cycle in the most effective manner for its products.
BSIMM was utilized to create BeatpulseLabs’s Product Security Baseline to assure basic security and privacy requirements are addressed. The amount of security validation incorporated during the life cycle for a product varies depending on the product's relative risk.
BeatpulseLabs designs security into Beatpulse’s Software to ensure a consistent, secure experience across your enterprise, whether it's providing role-based access control (RBAC), logging, authentication, or authorization.
BeatpulseLabs’s Software is also designed to integrate into your organization's security infrastructure through support of standards such as LDAP, SAML, OpenID, and even using your organization's identity store and security policies at the web level to facilitate single sign-on or public key infrastructure (PKI) support.
Additional embedded product security capabilities are documented in the BeatpulseLabs’s Software Trust Center (beatpulselabs.com/trust) as well as our online help.
BeatpulseLabs provides secure coding training based on Open Web Application Security Project (OWASP) guidelines and promotes awareness of the Common Weakness Enumeration (CWE/SANS) Top 25 most dangerous software errors.
BeatpulseLabs provides teams with secure coding checklists to further reinforce the importance of key security items that all product teams should address.
Basic items, such as malicious code discovery, have been incorporated into the build process for many years, utilizing multiple antivirus programs to minimize risk and false positive alerts.
BeatpulseLabs applies its most rigorous security measures for its foundational products of BeatpulseLabs's Software Enterprise, Software Online, and Software Pro. These products regularly undergo static code analysis, dynamic scans, third-party component analysis, and periodic third-party pen testing.
BeatpulseLabs continues to expand the amount of security validation it performs against all BeatpulseLabs’s Software products and seen in table 2 below.
Table 2: Key Attributes of BeatpulseLabs’s Security & Privacy Development Lifecycle


3. Software-as-a-Service Security
Api.beatpulselabs.com is BeatpulseLabs’s premier software-as-a-service (SaaS) content. BeatpulseLabs's security strategy for government-authorized offerings, such as Api.beatpulselabs.com, is based on an industry-standard defense-in-depth approach that provides security controls at every level including application, network, and facilities.
BeatpulseLabs is actively pursuing ISO 27001 certification of the European Union regional capabilities of BeatpulseLabs‘s Online and data processing systems.
Api.beatpulselabs.com is BeatpulseLabs’s premier software-as-a-service (SaaS) content. BeatpulseLabs's security strategy for government-authorized offerings, such as Api.beatpulselabs.com, is based on an industry-standard defense-in-depth approach that provides security controls at every level including application, network, and facilities.
BeatpulseLabs is actively pursuing ISO 27001 certification of the European Union regional capabilities of BeatpulseLabs‘s Online and data processing systems.
4. Vulnerability and Breach Response
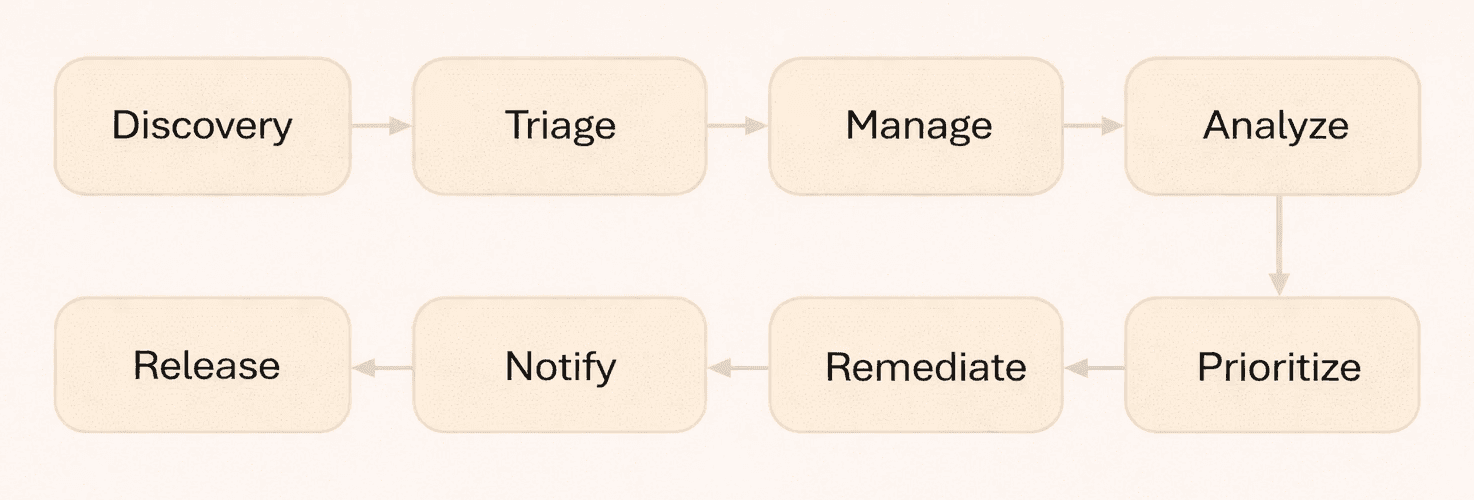
BeatpulseLabs has a Product Security Incident Response Team (PSIRT), which reports to the CISO-Products, to help shepherd security issues from cradle to grave, as shown in figure 3.
Vulnerability concerns can be submitted via BeatpulseLabs's standard support process or Trust Center security concern page, where the PSIRT team will be engaged.
To help prioritize efforts, BeatpulseLabs utilizes the Common Vulnerability Scoring System (CVSS) to determine the potential severity of the vulnerability and adjust for applicable environment factors.
Ultimately, the resolution of a reported incident may require upgrades to products that are under active support from BeatpulseLabs.
If an item requires a security patch, upon release, it is broadcast in the Trust Center "Announcements" section, which has an RSS feed that customers can subscribe to. BeatpulseLabs also announces patches through its Support site, blogs, and some end-user products to notify the user of updates when starting the application.
If an event were to occur where a customer's data being managed by BeatpulseLabs was confirmed breached, BeatpulseLabs will contact the customer within 72-hours.
BeatpulseLabs will coordinate with appropriate parties to investigate the security breach and perform remediation as necessary. BeatpulseLabs will provide updates to the customer with applicable information on a mutually agreed-on schedule.
BeatpulseLabs does not inform any third party of a breach of a customer's information and data without first obtaining the customer's prior written consent, unless required by law or court order.
Figure 3 - Product Security Incident Response Team (PSIRT) Workflow
BeatpulseLabs has a Product Security Incident Response Team (PSIRT), which reports to the CISO-Products, to help shepherd security issues from cradle to grave, as shown in figure 3.
Vulnerability concerns can be submitted via BeatpulseLabs's standard support process or Trust Center security concern page, where the PSIRT team will be engaged.
To help prioritize efforts, BeatpulseLabs utilizes the Common Vulnerability Scoring System (CVSS) to determine the potential severity of the vulnerability and adjust for applicable environment factors.
Ultimately, the resolution of a reported incident may require upgrades to products that are under active support from BeatpulseLabs.
If an item requires a security patch, upon release, it is broadcast in the Trust Center "Announcements" section, which has an RSS feed that customers can subscribe to. BeatpulseLabs also announces patches through its Support site, blogs, and some end-user products to notify the user of updates when starting the application.
If an event were to occur where a customer's data being managed by BeatpulseLabs was confirmed breached, BeatpulseLabs will contact the customer within 72-hours.
BeatpulseLabs will coordinate with appropriate parties to investigate the security breach and perform remediation as necessary. BeatpulseLabs will provide updates to the customer with applicable information on a mutually agreed-on schedule.
BeatpulseLabs does not inform any third party of a breach of a customer's information and data without first obtaining the customer's prior written consent, unless required by law or court order.
Figure 3 - Product Security Incident Response Team (PSIRT) Workflow


5. Privacy
BeatpulseLabs values the privacy of its customers, distributors, and partners, as it is a principal component of establishing trust. BeatpulseLabs has created a general company Privacy Statement and a Products & Services Privacy Statement Supplement to ensure that customers receive the level of privacy they deserve and expect. The privacy statements describe how BeatpulseLabs collects data and uses information you provide to us and are independently validated.
BeatpulseLabs supports alignment with the General Data Protection Regulation (GDPR), the California Consumer Privacy Act (CCPA), and has a Data Processing Addendum (DPA) containing Standard Contractual Clauses available within the ArcGIS Trust Center documents that customers can sign. Lastly, HIPAA eligible services are available for ArcGIS Online, which are backed by a Business Associate Agreement (BAA).
BeatpulseLabs values the privacy of its customers, distributors, and partners, as it is a principal component of establishing trust. BeatpulseLabs has created a general company Privacy Statement and a Products & Services Privacy Statement Supplement to ensure that customers receive the level of privacy they deserve and expect. The privacy statements describe how BeatpulseLabs collects data and uses information you provide to us and are independently validated.
BeatpulseLabs supports alignment with the General Data Protection Regulation (GDPR), the California Consumer Privacy Act (CCPA), and has a Data Processing Addendum (DPA) containing Standard Contractual Clauses available within the ArcGIS Trust Center documents that customers can sign. Lastly, HIPAA eligible services are available for ArcGIS Online, which are backed by a Business Associate Agreement (BAA).
Contact
For questions or legal concerns, reach us at support@beatpulselabs.com
For questions or legal concerns, reach us at support@beatpulselabs.com
